How can we help?
Let’s talk about how we can help you transform your business.
Contact us
With cyber threats continuing to increase in intensity and frequency every day, code security matters more than ever. There are a variety of strategies you can implement to help protect your applications and data, and multiple safeguards should be used together to ensure maximum protection. One effective way to safeguard your software is through a secure code review. Secure code review is a process involves systematically examining a source code to proactively identify and fix security vulnerabilities. By integrating secure code reviews into your development lifecycle, you can significantly enhance your application’s security, reduce the risk of breaches, and ensure compliance with industry standards.
Read on to learn more about the importance of secure code reviews and what the process looks like.
Secure code review is a critical practice in the software development lifecycle. The secure code review process aims to ensure that the code is not only functional but also resilient against potential threats and attacks. By reviewing code with a security-focused lens, you can detect and address weaknesses that could be exploited by malicious hackers.
Unlike traditional code reviews, which primarily focus on functionality, performance, and maintainability, secure code reviews specifically target security issues. These reviews are conducted by developers, security experts, or automated tools that scan the code for common vulnerabilities.
Secure code review can be conducted at various stages of the development process. It can be performed during the initial coding phase, as part of the continuous integration/continuous deployment (CI/CD) pipeline, or as a final check before deploying the application to production. The goal with secure code review and other preventive security measures is a shift toward DevSecOps – an environment where security is considered an integral part of the development process. The goal with such measures is to integrate security into the development process so that becomes a proactive rather than reactive measure.
By incorporating secure code review into your development practices, you can catch and fix security issues early, reducing the cost and effort required to address them later. This approach not only enhances the overall security of your applications but also builds a culture of security awareness among your development team.
Secure code review plays a vital role in the software development process, providing numerous benefits that contribute to the overall security and quality of your applications. Here are some key reasons why secure code review is essential:
Early Detection of Vulnerabilities
One of the most significant advantages of secure code review is the early detection of security vulnerabilities. By identifying issues during the development phase, you can address them before they become critical problems. This proactive approach helps prevent potential security breaches that could occur if vulnerabilities were left undetected until after deployment.
Cost-Effective Security Measure
Fixing security issues early in the development process is far more cost-effective than addressing them post-deployment. The cost and effort required to remediate vulnerabilities increase exponentially as the software progresses through the development lifecycle. Secure code review helps you catch and fix issues early, saving time, resources, and money in the long run.
Improved Code Quality
Secure code review not only focuses on identifying security vulnerabilities but also promotes better coding practices. By scrutinizing the code for security issues, developers are encouraged to write cleaner, more maintainable code. This process leads to improved overall code quality, making the software easier to maintain and extend in the future.
Compliance with Industry Standards
Many industries are subject to strict regulatory requirements that mandate secure coding practices. Secure code review helps ensure that your code complies with relevant security standards and regulations, such as OWASP, PCI-DSS, and GDPR. Adhering to these standards is crucial for avoiding legal and financial repercussions and maintaining customer trust.
Enhanced Security Awareness
Incorporating secure code review into your development process fosters a culture of security awareness among your development team. Developers become more knowledgeable about common security vulnerabilities and best practices for mitigating them. This increased awareness leads to more secure coding practices and a greater emphasis on security throughout the development lifecycle.
Reduced Risk of Exploitation
By systematically examining your code for security vulnerabilities, you significantly reduce the risk of exploitation by malicious actors. Secure code review helps ensure that your applications are robust and resilient against various types of cyber attacks. That ultimately helps you protect sensitive data and maintain the integrity of your systems.
Increased Trust and Confidence
When your applications are secure, your users and stakeholders have greater trust and confidence in your products. Secure code review demonstrates your commitment to security. That can help you build a positive reputation and strengthen relationships with customers, partners, and regulatory bodies. After all, customers really only want to work with companies that are dedicated to protecting their secure information.
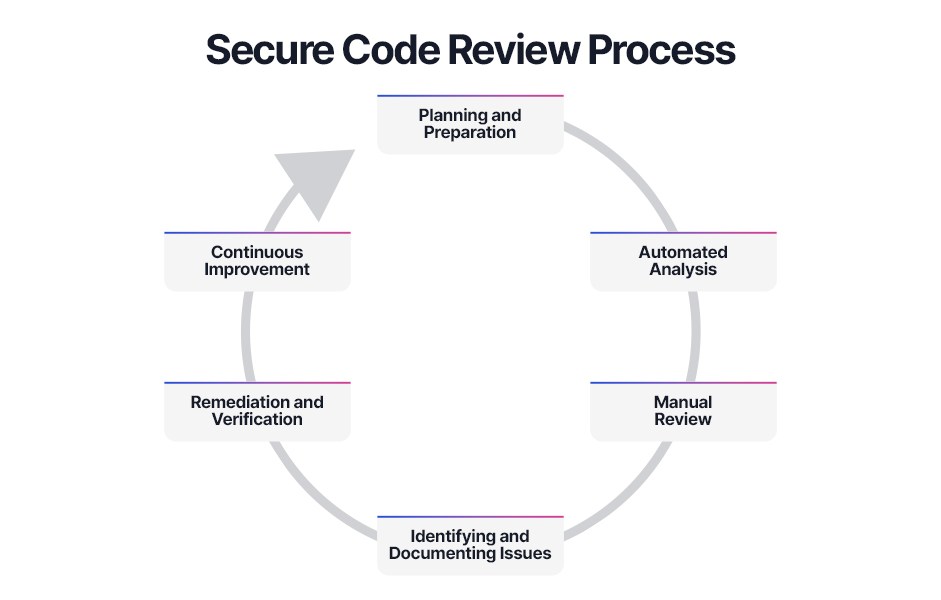
The secure code review process involves a series of steps designed to identify and remediate security vulnerabilities within your code. Here’s a detailed overview of the secure code review process:
Before starting the secure code review, it’s essential to plan. This stage involves defining the scope of the review, selecting the code to be reviewed, and assembling the review team. Key activities include:
Secure code reviews are often automated. Automated tools can quickly scan large codebases for common security vulnerabilities. These tools are effective for identifying issues such as SQL injection, cross-site scripting (XSS), and insecure configurations. That can include:
While automated tools are valuable, they cannot catch all security issues. Manual code review is an essential part of the secure code review process for identifying complex vulnerabilities that require human intuition and expertise. Here, you might perform:
As vulnerabilities and security issues are identified during the secure code review, they should be documented in detail. This documentation should include:
Once issues have been identified and documented, the next step in the secure code review process is remediation. This involves fixing the vulnerabilities and verifying that the fixes are effective. Key steps include:
Secure code review should be an ongoing process integrated into the development lifecycle. Continuous improvement involves:
Comtrade 360 is here to partner with your company to ensure that your application development process is secure from start to finish. Our security services help you integrate security into every stage of the development lifecycle. Whether you want to perform a security code review or add secure DevOps, we’re here to help.
Contact us to get started.